It’s been a long time since I blogged.
In fact, it’s my first blog after joining Accenture. Just enjoying the work experience and learning new things. In this span I learnt couple of new tools and technologies, and one of them is Team Foundation Server 2010.
For those who are not aware of what Team Foundation Server is? Here is a brief introduction; Team Foundation Server (commonly abbreviated as TFS) is a Microsoft product for collaborative software development projects and offers source control, data collection, reporting and project tracking.
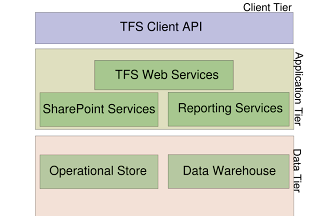
Team Foundation Server works in three-tier architecture: the client tier, the application tier and the data tier. The client tier is used for creating and managing projects and accessing the items that are stored and managed for a project, however TFS does not provides any user interface for this tier but exposes web services which client applications can use (e.g. Visual Studio Team System). The application layer contains the web services that are used by the client applications. It also includes a web portal and a document repository facilitated by Windows SharePoint Services. The web portal, called the Team Project Portal, acts as the central point of communication for projects managed by TFS. The document repository is used for both project items and the revisions tracked, as well as for aggregated data and generated reports. The data tier is SQL Server Standard Edition installation that provides the persistent data storage services for document repository.
Activities in Team Foundation Server revolve around Work Items. Work Item is a single unit of work that needs to be completed. Work Items can be of different types like Task, Requirement, Test Case, Bug, etc.
Visual Studio 2010 Ultimate offers an excellent tool for testers for carrying out the testing activities: Microsoft Test Manager 2010. It offers complete end to end testing of the application and managing the testing artifacts in Team Foundation Server.
Team Foundation Server (TFS) 2010 enables the users to manage test cases as Work Item(s). The complete description of the test case along with steps can be managed as single Work Item in TFS 2010.
Before migrating to TFS 2010 many test teams will be using MS Excel to manage the test cases (or test scripts). However, after migrating to TFS 2010, test teams can manage the test cases in the server but there may be need to get the test cases into excel sheet like approval from Business Analysts or sending it for review to a person who is not having access to the organization’s VPN.
Similar problem is been faced by me and my team, that once Test Cases are created in TFS there is no provision to export them to MS Excel. Thus I created an API “Test Case Export to Excel”
“Test Case Export to Excel” enables the users to export the test cases present in TFS as Work Item(s) to excel sheet. Thus, the users will have backward compatibility with the process they were using.
“Test Case Export to Excel” follows the concept:
- A Team Project consists of Test Plans.
- A Test Plan contains Test Suites.
- A Test Suite can contain Test Cases or Sub-Suites which in turn can contain test cases.
Image below shows the hierarchy explained above:

“Test Case Export to Excel” can export all the test cases present in a test suite to a excel file. If the selected Test Suite contains any Sub-Suite(s), then all the test cases present in the sub-suite(s) will also be exported to the excel file.
“Test Case Export to Excel (Beta)” is built on .NET Framework 4.0. Thus, .NET Framework 4.0 is required to be installed on the client machines to run “Test Case Export to Excel (Beta)”.
If .NET Framework 4.0 is not present on the client machine, then at the start of installation user will be prompted to install .NET Framework 4.0.
“Test Case Export to Excel (Beta)” is a GUI based simple tool that guides the users to export test cases from TFS to MS Excel.
“Test Case Export to Excel (Beta)” starts with screen as shown below:
1.1 Seleting the “Source”
Source for “Test Case Export to Excel (Beta)” is the Test Suite in Team Foundation Server that contains the test cases.
For selecting the Test Suite you are required to connect to Team Foundation Server and then connect to a Team Project.
For connecting to a Team-Project click the ellipses (…) button next to Team-Project text box. You will be presented with a screen shown below with option to connect to a Team-Project.

If there is no Server present in the dropdown box then click the “Servers…” button to add a Server.
You will be presented with dialog to “Add/Remove Team Foundation Server”.

Click on “Add…” button to add details of Team Foundation Server you want to connect.
In “Add Team Foundation Server” dialog you can enter the details of Team Foundation Server that contains your Team-Project.

After successfully connecting to Team-Project all the Test Plans present under the selected “Team-Project” will be populated automatically in the “Test-Plan” dropdown box. (If there are no Test Plan present in the dropdown box then the selected Team-Project doesn’t contains any Test Plan).
Select a “Test Plan” from the available Test Plan(s) in the Test-Plan dropdown box. Based on the selected “Test Plan”, Test-Suite dropdown box will be populated with all the Test-Suites present in the Test Plan.
Note: Only the Test Suites present directly under selected Test-Plan will be populated in the Test-Suite dropdown box. No Sub-Suite(s) present under any of the Test-Suite will be populated. However, during export if the selected Test-Suite contains any sub-suite(s), then the test cases under the sub-suite(s) will also be exported.
1.2 Seleting the “Destination”
Destination is the location where the excel file with exported test cases will be saved.
Select the folder location using the “Browse…” button where you want to save the file.
Specify a valid file name for the excel file.
1.3 Exporting
After entering both “Source” and “destination” details click on “Export” button.
If the fields are populated correctly, export process will start; otherwise error message will be displayed and you are supposed to correct the error(s) before you proceed.
During export, mouse cursor will be shown in busy state. The export may take some time depending upon the data to exported and network speed.
After successful export, a confirmation message will be displayed.
Product information i.e. version detail and developer information is available by clicking on “About” button.
Current product version is “Beta” version.

However, there are some known issues with the current version.
- If there already exists a file with same name as specified by the user in the specified location, then a dialog box is displayed to replace the file with “Yes”, “No” and “Cancel” buttons. If user clicks “Yes” button, the existing file is replaced with the new one; whereas if user clicks “No” or “Cancel” button, application throws “Fatal Error” and terminates.
- If client machine is having version of MS Office higher that 2003, then a compatibility warning is displayed with “Continue” and “Cancel” button. If user clicks “Continue” the excel file is saved successfully; but if user clicks “Cancel”, application throws “Fatal Error” and terminates.
I will try to address the above mentioned issues in the upcoming version with few more functionalities.













